Afero has two rules:
#1: Users come first
#2: See Rule #1
Users are everything.
That's why we designed our platform to protect user privacy while also making your products a joy to experience. Why go to so much trouble to make everything secure, speedy and scalable? Because that's what users of your brand deserve.

Secure Foundation
If it's a connected device, it's also a potential target for cyber attack. This is why we help architect security and privacy from the foundation.
End-to-End Security
Guarantee device security from supply chain to customer, device to cloud, cloud to mobile app, user to device.
Trusted Devices
Get hardened security that makes each device uniquely protected with hardware roots of trust where needed, through the supply chain to the device, mobile app, and cloud.
Secure Connections
Afero allows devices to communicate securely through any available channel for better security, resilience, and ultimately a superior customer experience.
Secure the Data
All data flows through multiple "tunnels" of protection, encrypting data in transit and authenticating all data paths.
Secure Onboarding
Customers want it all to be easy and fast, but not at the expense of security.

Market Speed
Rolling out a robust IoT solution does not have to take months or years. Our integrated IoT solution features everything you need to create a successful line of IoT products, giving you maximum control with minimum effort.
Rapid Dev
Afero gives you a low-code drag-and-drop development environment that is already aware that there is an embedded device, that mobile apps are required, and that cloud back-ends need to be in sync.
Flawless Onboarding
Through Afero's simple, secure onboarding process, you can expect to experience everything from higher customer retention rates to fewer customer support issues.
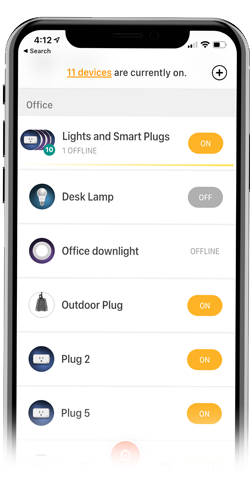
Responsive Devices
Afero's approach to improving customer experience has proven to benefit not only the customers, but the people that create smart products.
Customer Success
We've designed our app to be as simple as possible, allowing customers to enjoy their smart products without worrying about the setup process or dealing with failures. Automatic failover from Afero saves time, saves aggravation, and sometimes saves the day.
Hardened Security
We ensure top security between device and cloud using unique key exchange, weapons-grade encryption, and countermeasures for both individual device and the supply chain, taking security to new heights and widths.

Secure Foundation
If it's a connected device, it's also a potential target for cyber attack. This is why we help architect security and privacy from the foundation.
Build-it-alone trap
Afero offers the best solution: tap the best IoT platform on the market, get to market fast, deliver a great customer experience, and maintain control.
Total Solution
IoT is not one thing or even a few things. It's layers of proven expertise, across a broad spectrum, all built into the Afero Platform.
Spend Wisely
By leveraging the Afero Platform's tools, such as Afero edge, cloud, developer tools, and core/cross platform services, you can build and provision more profitably.
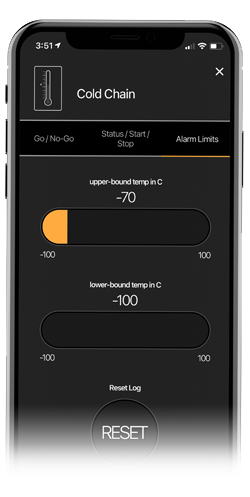
Data Trove
Monitor and manage your IoT deployment in a single dashboard, speeding up your time-to-market and making sure you have everything you need once you get there.
Last-Mile Brilliance
Afero's patented onboarding process uses a combination of security and communication technologies to create a simple and seamless experience that enables customers to connect easily and, more importantly, fully understand the usefulness of their IoT product.